Secure, Automated Networks Designed for Oil, Gas, and Energy
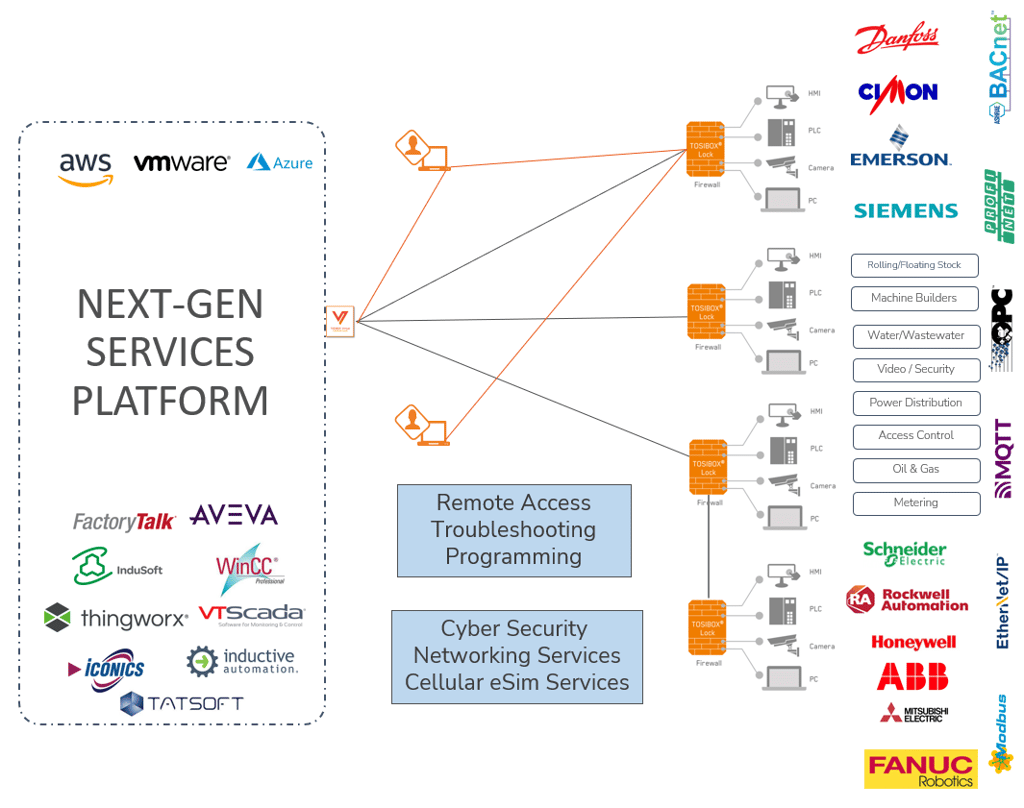
The days of trying to build and scale OT networks with Traditional IT solutions are gone. Incorporating a mixture of IPSEC tunnels, port forwarding, private APN's, cell modems, Cisco, Fortinet, Palo Alto, and various other IT tools have proven to be overly complex and expensive.
The Tosibox platform has taken all of the complexity of these traditional networking tools and automated them in 10 seconds. Reduce costs, complexity, and cybersecurity risks of traditional networking through 3 simple steps explained below.

The Tosibox Platform is your OT networks central management Hub. From your platform you can:
- Create always on VPN connections to any on prem. or hosted environment for data collection
- Manage user access down to the port, protocol, IP, or MAC ID level
- Time restrict user network access
- View a real-time user audit log
- Build access groups for simplified data, site, and user management
- Manage data connections to multiple hosted applications
The Platform is a virtual machine that can be hosted in Azure, AWS, The Tosibox Data Center, or any other cloud or on prem. environment. It is your platform, you host it where you choose.
Site installations with Tosibox edge nodes are as plug-and-go as it gets. Clip on din-rail, provide power, plug into any ethernet capable device or switch, and provide internet. Once installed, you have built in:
-Automated Firewall for network segmentation and device security
-Taken away static IP's and closed off inbound ports
-Layer 2 and 3 capable point-to-point VPN connectivity
-Remote access for your team or vendors through physical-first MFA
-Site to Cloud VPN tunnels built automatically through checkboxes
-Auto-failover between multiple internet sources (ethernet, WiFi, cellular, and/or satellite)
-Protocol agnostic, Layer 2 capable platform allows you to connect any ethernet capable devices and speak any protocol you choose.
-Have multiple sites communicate on the same network through checkboxes in the platform
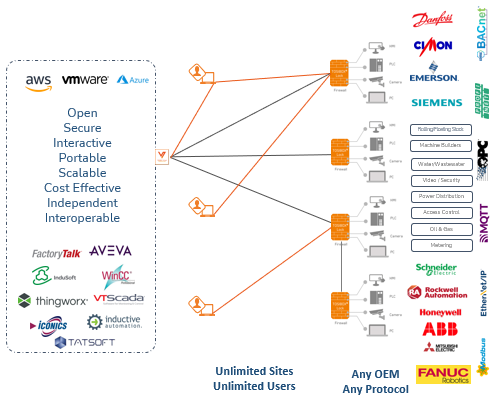
Provide user access to your OT network through physical-first multi factor authentication. This takes traditional MFA (username and password) to a higher level by limiting network access to a specific device that has been serialized and approved. Adding users to your network is as simple as generating a serialization, sending it to the user, and checking boxes of what you want them to have access to.
-Access provided through physical USB keys or software serializations for PC’s, Android, or IOS devices.
-All user access connections are through 256-bit AES encrypted VPN tunnels
-Access can be provided via Layer 2 or Layer 3 connections
-Can be restricted down to the port, protocol, MAC ID, or IP level
-User access can also be time restricted
-Access can also be provided or withdrawn immediately
-Users can have access to an unlimited number of sites or devices
-Devices can have an unlimited number of users accessing that device

If you watched the video or read through the steps above, you have just learned how to build cybersecure OT networks in seconds. The next step is to see it in action within your own application.
Tosibox offers a 30 day risk free proof of concept that is tailor fit to your specific goals. Click the button below to schedule a PoC discussion.
As part of a proactive cyber posture, the CISA, FBI, and NSA recommend:
TOSIBOX Is Your Dedicated Operational Network Platform:
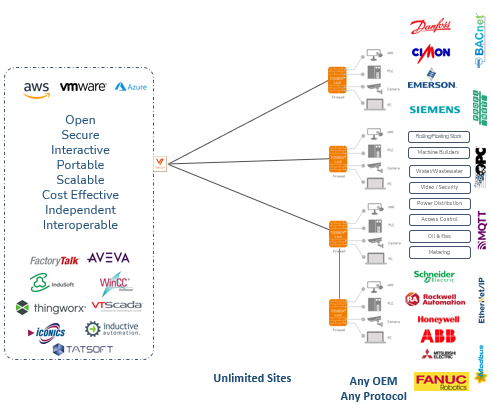
The Tosibox Platform is a fully automated OT platform that embeds industry leading cybersecurity in every connection automatically.
The Tosibox Platform has been approved by IT groups of global enterprise organizations in over 150 countries, and here is why:
With the Tosibox Platform, you can create point-to-point Layer 2 or 3 capable VPN connections to equipment at the edge in 10 seconds. Once a network has been established, you can manage user access to equipment through simply checking boxes to provide new users cyber secure remote access to equipment at the edge.
The platform is also completely protocol agnostic, meaning, use any manufacturers ethernet capable equipment and speak any protocol you desire. If there is an ethernet port, it will work with Tosibox.
Creating always on VPN connections to a hosted environment for data collection is as simple as checking boxes. No IPSEC tunnels, Static IPs, or building out port forwarding channels. The Tosibox Platform automates cyber secure, always on connectivity from equipment at the edge to your data analytics applications in the cloud or on prem.
Host your data and applications wherever you choose, that could be in the Tosibox Tier 4 OT Data Center, AWS, Azure, or in an On Prem. Server.
You can also use whatever data applications you desire. If you already have an application built and hosted, no problem, Tosibox will seamlessly integrate. If you are looking to build your own platform, Tosibox is here to help.
Adding or removing users from the network is as simple as checking boxes to provide true physical first multi-factor authentication. This access can be time restricted, or restricted down to the port, protocol, network, or MAC ID level.
Audit logs of user access times and devices is stored in the Tosibox platform for accurate user management and time stamps.
The Tosibox platform was designed with OT in mind. Implementing Tosibox as your OT network solution provides full network segmentation from the IT side, setting the OT network behind its own cybersecurity. This protects your OT network from cyber vulnerabilities or attacks on the IT network.
Even though you are creating IT/OT network segmentation with the platform, there is still capability embedded for seamless integration with existing enterprise networks and corporate applications.
The Tosibox Cloud is a network of Tier 4 Datacenters. We understand the critical nature of Operational Infrastructure and Data which is why we feel our hosting EXCEEDS the out-of-the-box capabilities of the large hyperscaler platform. Highlights for the datacenter component of Tosibox Hosting and Managed Services includes:
Tosibox edge nodes can come ethernet/WiFi/Cellular (dual-sim integrated modem), and Satellite capable. We can select the best fit based on your application and network requirements.
Within the edge node settings is the capability to set the WAN priority. This is configured with a drop down menu to automatically fail-over between multiple internet sources.
Gone are the days where you are tied to one carrier or internet source. Setting up fully-redundant networks through the Tosibox platform has been simplified and automated.
-Proj. Example:
Capable Cellular Carriers:
-TosiSim Quad Carrier Sim (More Info in images below)
-All main cellular carriers including iNet LTE